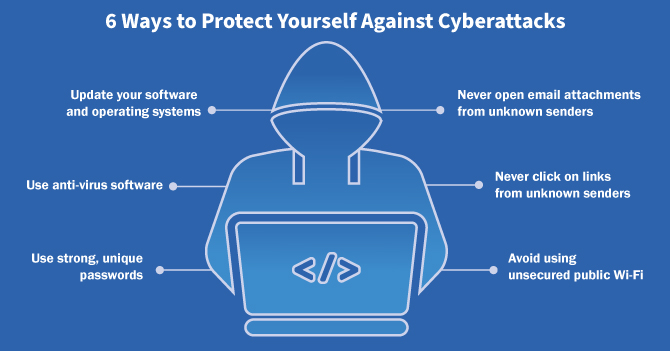
Cyberattacks have been on the rise for years and show no sign of slowing down. Aside from the obvious impacts of potentially losing one’s funds and spending time and effort to attempt recovery, cyberattacks often have other effects on victims. In many cases, the victim of a cyberattack will experience increased stress levels, a sense of vulnerability, and disrupted sleep patterns. Falling victim to a cyberattack can disrupt many aspects of life, that’s why it’s crucial for everyone to make sure they’re doing everything possible to protect themselves from cyberattacks. Here are six ways you can protect yourself from cyberattacks.
-

Update your software and operating systems. Accept every update when offered – these provide the strongest, and most current, protection. Keeping your software and operating systems up to date may seem like an annoyance to take care of. You might even find yourself constantly clicking “Remind Me Later” when prompted to make an update because you’re in the middle of something. Updating your system is more important than it can seem, though. One of the most important updates that you’re making are security updates. Companies that build software or make electronic devices are constantly monitoring for security threats and testing for holes in their systems. When they find a hole, patch it, and put it in an update, you can protect yourself from one of the ways a hacker could get to your personal information. Turning on automatic updates can help take it off your mind while also keeping your systems as current as possible.
-

Use anti-virus software. This software will detect, and remove, threats in real-time. This is one way to protect yourself from hackers that is very powerful but doesn’t require much effort on your part. Installing anti-virus software gives you peace of mind knowing that in the background, your device is being scanned for malicious software – often referred to as malware. The software will look for signs of known malware to detect it’s presence, warn you, and remove it for you, depending on the anti-virus package you choose. New kinds of malware and known malware that has been updated are discovered every day – another reason that keeping software, like anti-virus software, up to date is so important.
-

Use strong, unique passwords across all your online accounts. Vary your use of capitalization, symbols, letters and numbers. In 2022, over 24 billion passwords were exposed by hackers and 80% of those confirmed breaches were related to stolen, weak, or reused passwords – not very surprising given that 96% of the most common passwords can be cracked by hacking tools in less than one second, according to Norton. It’s reaffirmed every year: as hackers and their tools get more advanced, weak and reused passwords are a bigger and bigger security risk. According to a study done by cybersecurity firm Hive, a 9-character password using only lowercase letters can be cracked in as little as 3 seconds. Even a 10-character password using numbers, upper and lowercase letters, and symbols can be broken in 2 weeks. However, if you extend that to 11 characters, it goes up to 3 years, and 12 characters makes it 226 years. The statistics show that it can take a frighteningly small amount of time to hack a password, but increasing length and complexity can have exponential benefits to your cybersecurity. If you’re worried about remembering your passwords, a password keeper can be a great tool to consider.
-

Never open email attachments from unknown senders. These can download/install malware onto your device. Be cautious with emails from unknown senders, especially with any attachments. If you do not know the sender and it’s not an email you were expecting, never open any attachments. Even if it looks like the email came from someone you know, check for red flags like odd formatting or misspellings in the email, or spoofed email addresses that are made to look like someone you know. Hackers will disguise malware as whatever they are pretending to attach to the email, and when you download the attachment, it can install the malware onto your device. Familiarize yourself with common email scam tactics and do not open any suspicious attachments from senders you do not know.
-

Never click on links from unknown senders. Again, it’s key to be wary whenever dealing with unknown senders. In the same way that a phony attachment from a hacker can download and install malware onto your device, a link can do the same thing. Warning signs to look out for include any offer that seems too good to be true, like winning a lot of money or a new phone. On the other hand, messages that are very urgent or even threatening, like mentions of arrest or owing a lot of money, are also a tactic often used by hackers to get people to click on bad links. It’s always important to be vigilant when it comes to unknown senders that wind up in your inbox.
-

Avoid using unsecured public Wi-Fi. These networks leave you vulnerable to attacks. It may be tempting to use a public Wi-Fi network but even if it’s convenient, these networks can expose you to cyberattacks. Since the network is unprotected, it’s as easy for a hacker to get onto the network as it is for you. This could potentially provide them easy access to your devices, files, and personal information. Many people use public Wi-Fi as a last resort when they can’t connect using cellular data, while others use it to save their cellular data. In the short term it might seem like a good idea, but remember the potential long term risks. If you are going to use public Wi-Fi, then use a VPN to protect yourself.


Comments